You might believe that a strong password policy will be adequate to safeguard your cloud assets and code, but this is untrue. The human mistake will always prevail over carefully considered procedures and a security-conscious society. Human error is at blame for as much as 95% of all security breaches. How can human mistakes be prevented? by comprehending Identity & Access Management (IAM), its advantages and disadvantages, and using the appropriate tools to address those disadvantages.
What Is IAM (Identity & Access Management)?
Who has access to what digital resources are defined and maintained by a set of policies, tools, and apps known as identity and access management (IAM)? Access to code repositories, CI/CD pipelines, internal networks, wikis, platforms as a service, logs, and even Slack are all part of DevSecOps. Almost all of the resources you and your business utilize must only be accessible to those who truly need them.
What Do IAM Tools Do?
In order to manage identities (users) and access, identity and access management (IAM) tools are used (authentication and authorization). IAM tools are designed to simplify all facets of managing user privileges and accounts.
An IAM solution will often allow you to define a policy. The duties of users will thereafter be decided by this policy. Permissions will be specified for each role that is defined. Access to particular resources is permitted by these permissions.
Core features of IAM solutions usually include:
- A database listing users’ names and access rights
- Instruments for granting, overseeing, altering, and revoking access rights
- A recording and reporting system for access history and auditing
Security professionals are needed to develop and manage the policies in some IAM systems because of their complexity, such as AWS IAM. Other systems provide easier interfaces that anyone with technical knowledge can use to set up their regulations. It is important to keep in mind that this setup’s simplicity could be a trap because poorly specified policies could lead to security lapses.
Why You Need To Employ AIM
Effective resource allocation
IT departments rely on cloud service providers to give useful data, but it’s thought that most businesses waste licenses by not using them to their full potential. Salesforce (40%) Office 365 (38%) and Zoom (29%) are significant amounts of wasteful resources that a firm still has to pay for. Additionally, 88 percent of IT executives think that a centralized tool is required to find areas where their resource allocation is lacking.
Security
The great majority of IT specialists believe that authorized SaaS application usage on their networks poses a significant security risk. However, only 50% of IT specialists are confident in their capacity to keep an eye on permitted SaaS usage. Utilizing an IAM tool significantly improves your capacity to carry out your duties accurately and effectively, cutting the time it takes to onboard a new developer from an average of seven hours to just a few mouse clicks.
Scalability
If you believe your company is too small to require an AIM, you are probably mistaken. Your company probably employs at least four SaaS, according to a count you can make. And even while that does not have the same breadth as 100, it still calls for security, monitoring, and appropriate allocation.
Moreover, having a solution to handle everything in advance of the deadline makes sense as businesses expand and use more SaaS applications.
Top 11 Identity & Access Management Tools in 2021
Given that the majority of company resources and assets are now digital in some fashion, it is understandable why there is such a wide range of IAM solutions and supporting technologies. Solutions cover a variety of industries, target companies of various sizes, and have a flexible feature set to meet a range of demands.
1. Auth0
One of the top cloud authentication services around the globe is Auth0. It offers developers working on your web application a simple out-of-the-box experience for setting up authentication. A feature-rich dashboard for managing users, SSO integration, multi-factor Authentication, additional security measures, and applications is also available from Auth0 in addition to a super-simple setup for the login box.
2. SpectralOps
We believe that Spectral complements IAM in a very important way, even though it is not exactly an IAM solution. Both manually and automatically can be granted access. Typically, programmatic access is granted using “Secrets” and “Keys,” which can be improperly maintained. No matter how strong your company’s security culture is, mistakes are still made by humans.
The Big Three In Cloud Services
Each of the integrated IAM services offered by AWS, Google Cloud, and Azure is distinct. These services are meant to be used in conjunction with the associated cloud computing solutions. Each caters to the unique design of its platform as result.
Look beyond IAM’s purview while comparing pricing and offerings when deciding between the three. Using the IAM provided by the cloud solutions provider your company already works with is frequently (but not always!) the right decision.
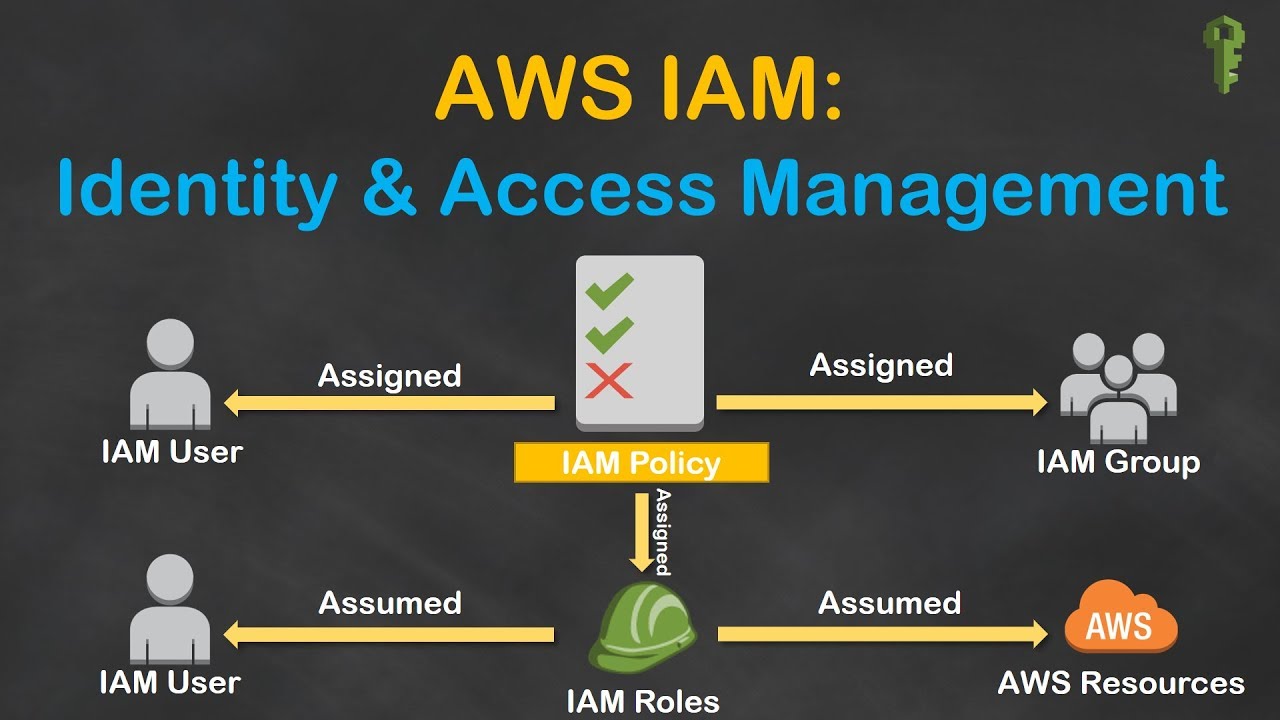
3. AWS Identity & Access Management
AWS is the industry leader in everything cloud-related, and they also rank well in the security and IAM fields. Organizations frequently select AWS because doing so gives them the security of working with a market leader. AWS has cloud solutions for every requirement, but they are complicated and have a long learning curve.
4. Microsoft Azure Active Directory
Due to the service’s unusual names, organizational structure, and pricing compared to most other services in the industry, Microsoft’s identity and access management solutions can be a little perplexing. There may be a steep learning curve if you are switching from another set of security tools. Microsoft has a small ecosystem all to itself.
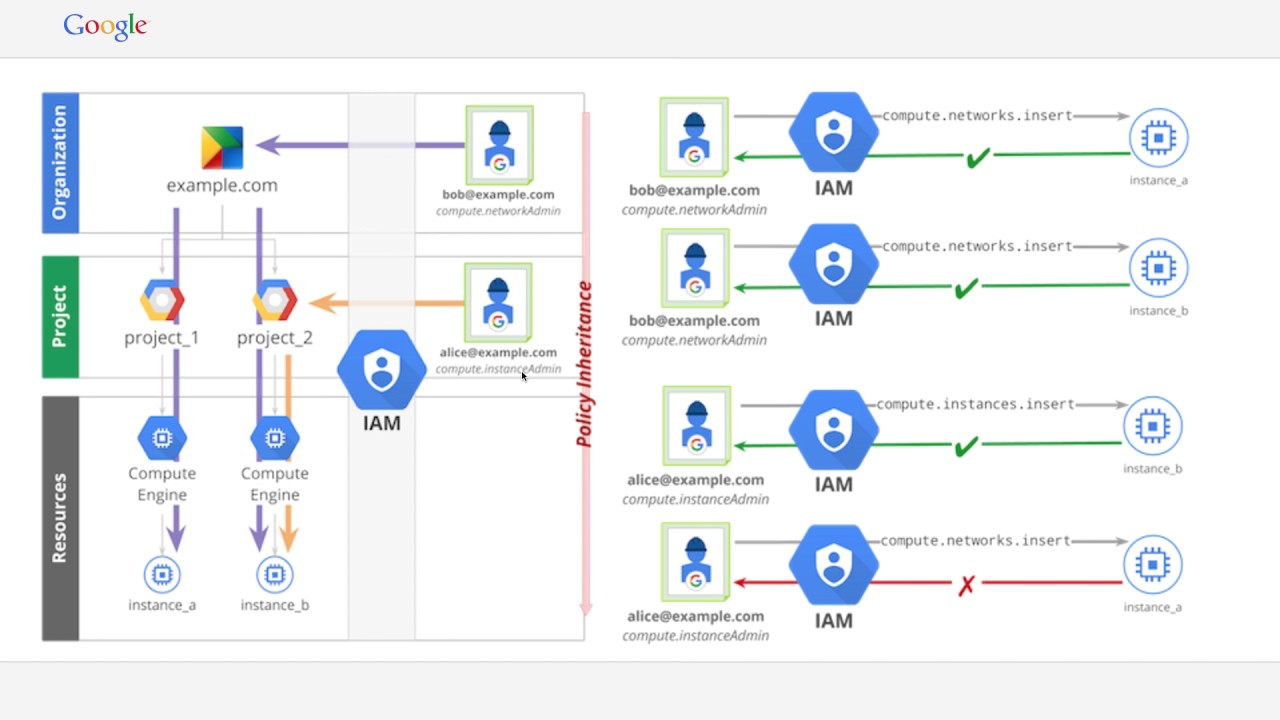
5. Google Cloud Identity and Access Management (Cloud IAM)
A google account is used by around one-third of all emails sent and received worldwide. Any firm may be sure that the great majority of their cloud users have a Google account because there are 1.5 Billion active Gmail users worldwide. In light of these facts, it is reasonable to choose Google Cloud as your IAM.
6. IBM IAM
You undoubtedly already know that IBM is a leader in artificial intelligence, but they use it for more than just teaching chess computers. Excellent addition to an IAM is IBM Security MaaS360® with Watson, a ground-breaking AI solution for endpoint security management. But IBM does more than that. When you choose IBM for your IAM solution, you also benefit from their experience with complex computing initiatives.
7. OneLogin
With the use of an accessible and well-documented API, OneLogin’s technology enables SSO (Single Sign-On) while using external SaaS and integration with any apps you may have. With AWS, SalesForce, and many other platforms and services, it can be integrated quickly. User experience is prioritized in their design. The goal is to maintain workflows as simple as possible while minimizing user discomfort.
8. Okta
Okta is a labor-management platform and development tool for backend user identity. This adaptable system seeks to serve as a one-stop shop for all IAM requirements. At the moment, Okta’s lack of passwordless options forces users to frequently change their passwords. Users have also reported some technical difficulties with logins.
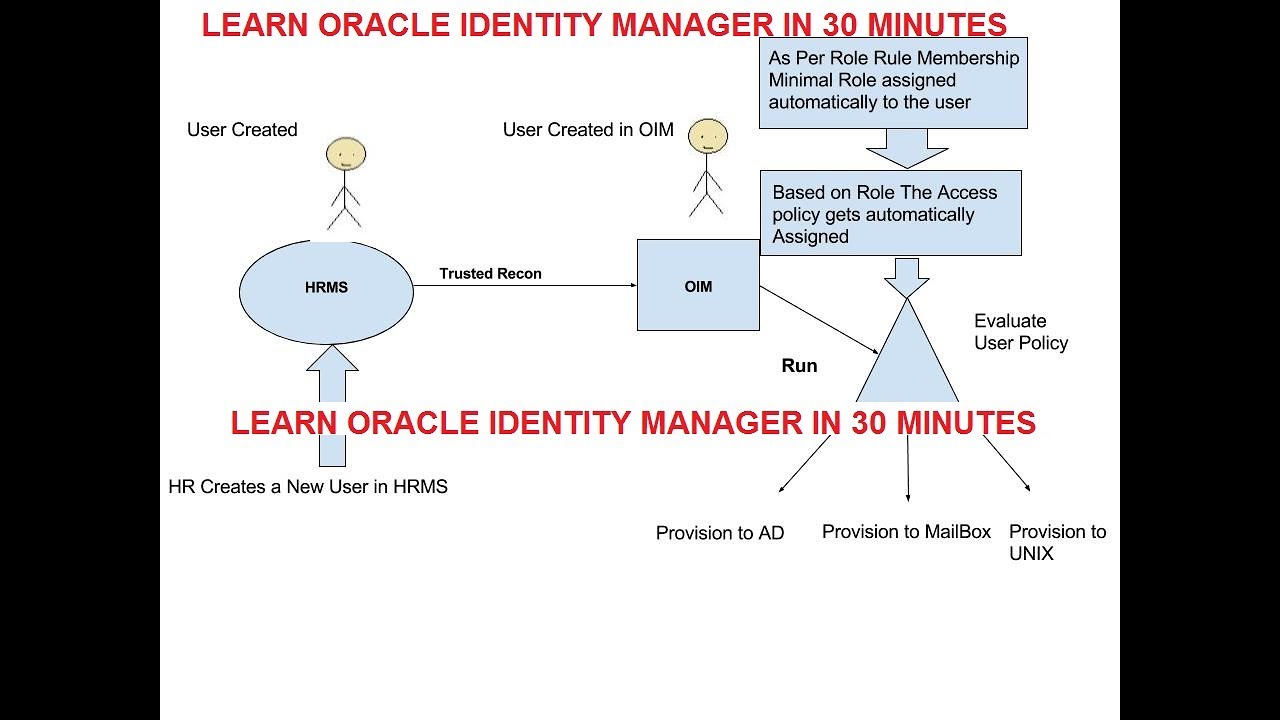
9. Oracle Identity Management
Despite not having the same level of cloud presence as Google, Microsoft, and Amazon, Oracle is nevertheless a major player in the tech sector. The Oracle system is adaptable and ideal for expanding enterprises that must continuously modify their rules. The Oracle product line is divided into two categories. The 12c is a more fundamental product that ought to meet the needs of businesses with less intricate systems.
10. Ping Identity
Ping Identity, as the name suggests, is an identity-first approach that combines MFA (Multi-factor authentication), device identity, and user behavior. Other IAM domains like SSO, Data Access Governance, and User Directories are no match for Ping Identity. There are some issues with the product, mostly related to its expensive price and API communications.
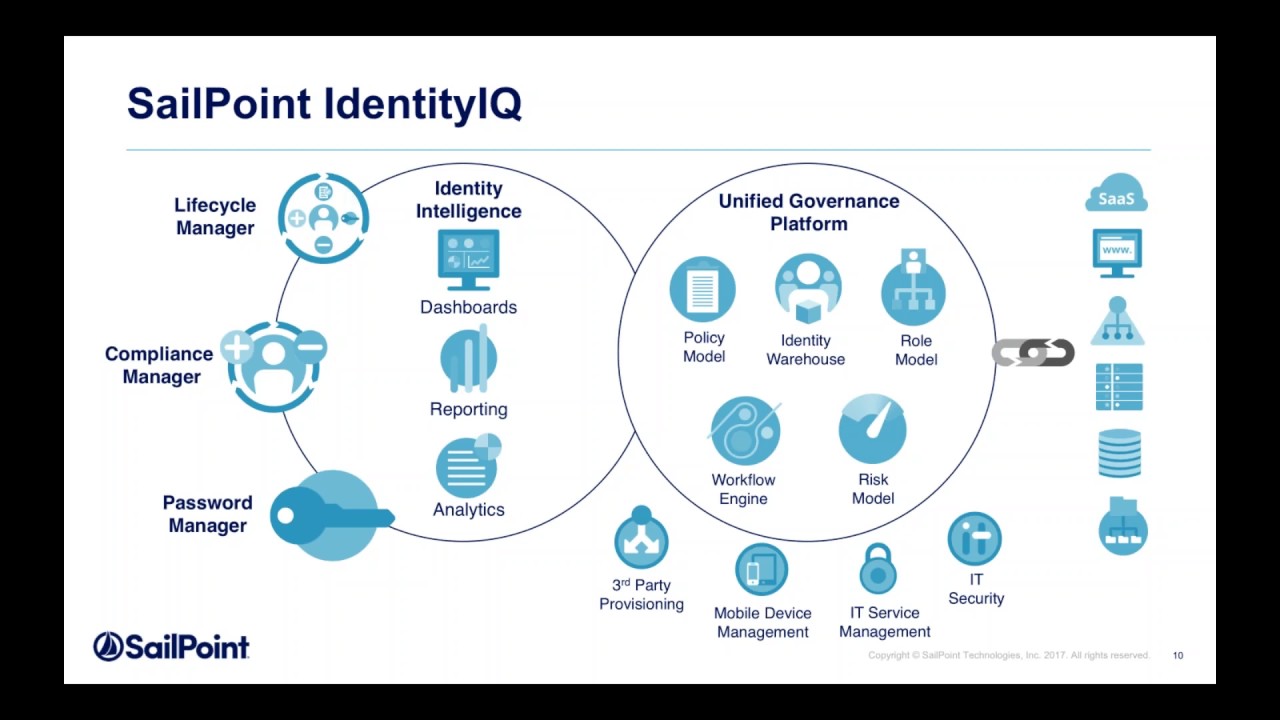
11. SailPoint IdentityIQ
IdentityIQ, a component of SailPoint’s product line, combines IdentityIQ, IdentityNow, Security IQ, and Identity AI into a single IAM application. Data governance is one of SailPoints’ core features, which makes it a suitable choice for businesses that handle a lot of data. It excludes SSO, though, and has a severe learning curve.
Summary
It’s difficult to choose the best IAM for the job. There are many options available, and the majority of them share a fundamental set of characteristics.
You should generally start by determining whether the solutions offered by your current main cloud platform, such as Azure, Google Cloud, or AWS, satisfy your demands. The best option may be something like Auth0 if you’re creating an application.
Regardless of the IAM you choose, it’s imperative to use a covert scanner like Spectral Ops. Because without it, human mistakes might cause even the most reliable IAM systems to fail. Any leak of a secret indicates that all of your security measures were useless, and you might as well not have had them at all.